From LLMs to Agents: How BigID is Enabling Secure Agentic AI for Data Governance
Understanding Large Language Models (LLMs) Large Language Models (LLMs) form the foundation of most generative AI…

Understanding Large Language Models (LLMs) Large Language Models (LLMs) form the foundation of most generative AI…

Welcome to the January 2026 edition of WPBeginner Spotlight! This month, we’re looking at new tools…
There is a pervasive myth in the web development community: “WordPress is for novices. Real developers…
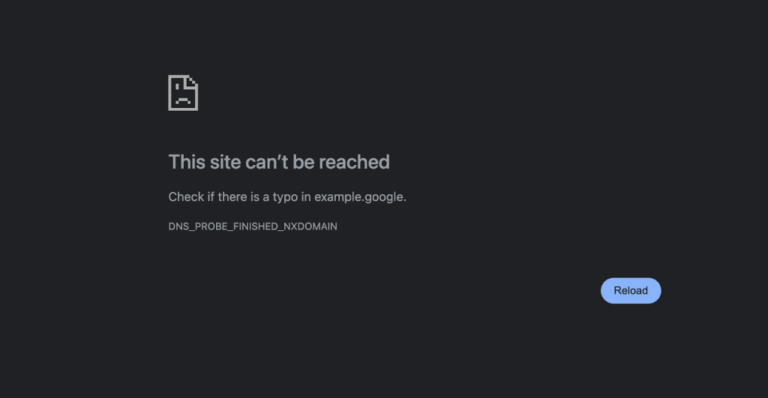
Are you seeing the “This site can’t be reached” error on your site? This error is…

Join my school community: https://www.skool.com/cyber-scrilla-7852/about
Most users tap Pay on Android and assume it’s simple. Behind that one tap, your app…

I once tried to buy a pair of headphones I really wanted. But when I got…

Turns out Microsoft’s Copilot assistant is actually very helpful… to hackers. ARTICLES:https://arstechnica.com/security/2026/01/a-single-click-mounted-a-covert-multistage-attack-against-copilot/https://www.zdnet.com/article/copilot-steal-data-reprompt-vulnerability-microsoft/ SUPPORT: https://funkytime.tv/patriot-signup/MERCH: https://funkytime.tv/shop/FUNKY TIME…
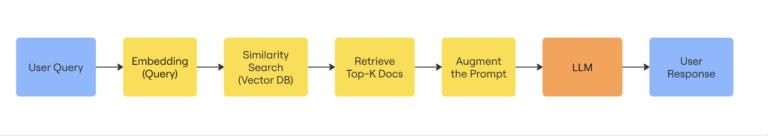
Retrieval-augmented generation (RAG) has emerged as a powerful technique for building AI systems that can access…
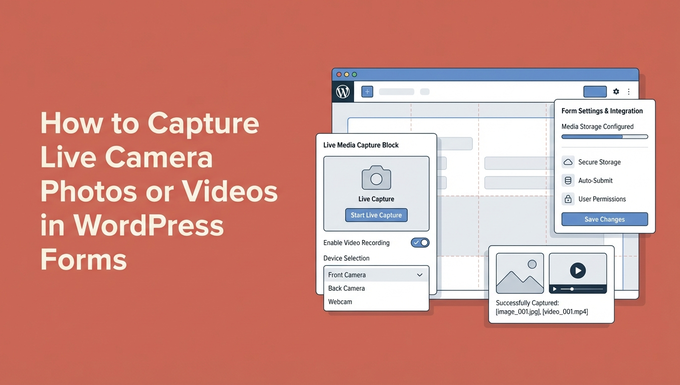
I used to ask people to email me their photos for my website. Profile pictures for…

It is often assumed that encryption is the gold standard method for securing assets in the…

Most WooCommerce store owners hit a wall trying to turn visitors into paying customers. Sales trickle in…
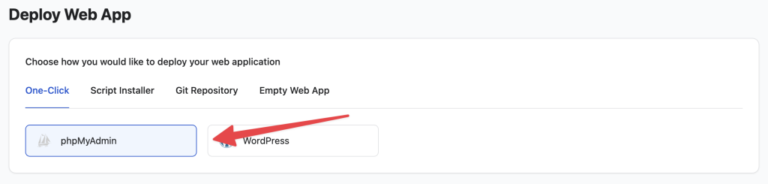
We are happy to bring One-Click phpMyAdmin feature in RunCloud for you. Using this new feature,…
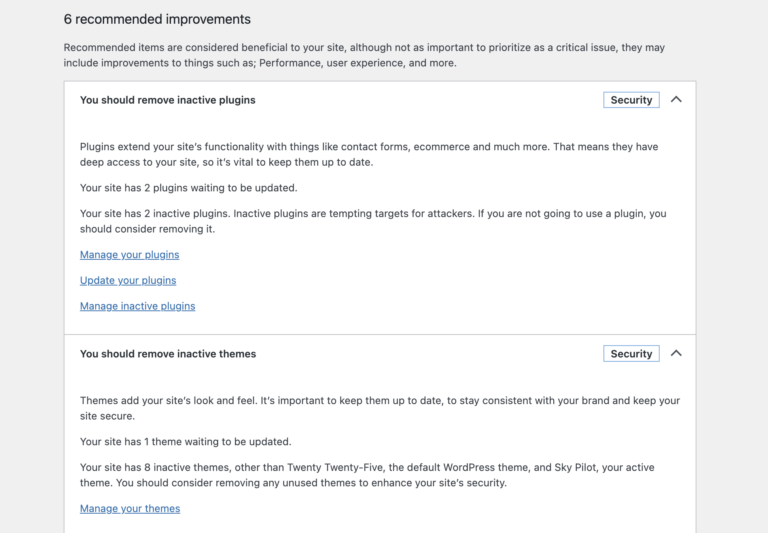
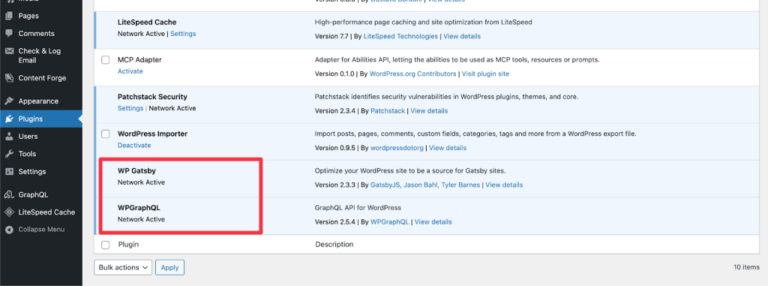
Unused WordPress plugins can slow your site down and weaken your security, even when they’re deactivated….
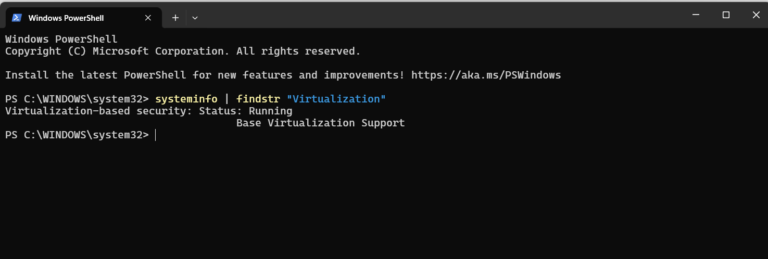
Although Linux remains the easier and more efficient platform for most containers, Windows Server still plays…