A unicorn-like Spinosaurus found in the Sahara
But there was one thing that made S. mirabilis different from S. aegyptiacus. The word “mirabilis”…

But there was one thing that made S. mirabilis different from S. aegyptiacus. The word “mirabilis”…

Get Tangem (30% off + free Bitcoin): https://tangem.com/pricing/?promocode=CYBERSCRILLA&promocode=NYEXTRA26 Join my private crypto security community: https://www.skool.com/cyber-scrilla/about Tangem…

Hello, our dearest DZone Community! Last year, we asked you for your thoughts on emerging and…

If you’ve been blogging for a while, you probably have dozens (or even hundreds) of posts…

Introducing the all new MacBook Neo! Apple’s most feature-proof laptop yet! SUPPORT: https://funkytime.tv/patriot-signup/MERCH: https://funkytime.tv/shop/FUNKY TIME WEBSITE:…
WordPress 7.0 Beta 3 is available for download and testing! This beta version of the WordPress…

Apple just announced their new M5 Pro & M5 Max MacBook Pros and everyone is happy…

Google and other browser makers require that all TLS certificates be published in public transparency logs,…
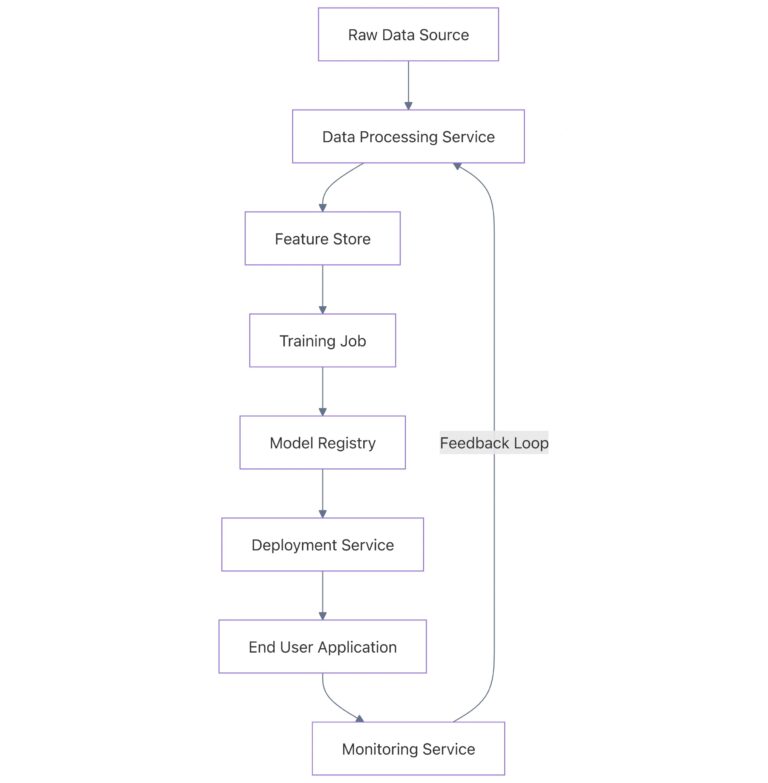
As Artificial Intelligence (AI) shifts from experimental prototypes to mission-critical production systems, the complexity of managing…

Introducing the “old-new” Galaxy S26 Ultra! SUPPORT: https://funkytime.tv/patriot-signup/MERCH: https://funkytime.tv/shop/FUNKY TIME WEBSITE: https://funkytime.tv FACEBOOK: http://www.facebook.com/SamtimeNewsTWITTER: http://twitter.com/SamtimeNewsINSTAGRAM: http://instagram.com/samtimenews…

Get Tangem (20% off & free bitcoin): https://tangem.com/pricing/?promocode=CYBERSCRILLA&promocode=NYEXTRA26 Get Arculus ($10 off use code CYBERSCRILLA): https://arculusholdingsllc.pxf.io/JkbxRr…

Welcome to another exciting edition of the WPBeginner Spotlight! February 2026 has been an incredible month…
WordPress 7.0 Beta 2 is now ready for testing! This beta version of the WordPress software…

Microsoft somehow keeps finding ways to make Windows worse. SUPPORT: https://funkytime.tv/patriot-signup/MERCH: https://funkytime.tv/shop/FUNKY TIME WEBSITE: https://funkytime.tv FACEBOOK:…
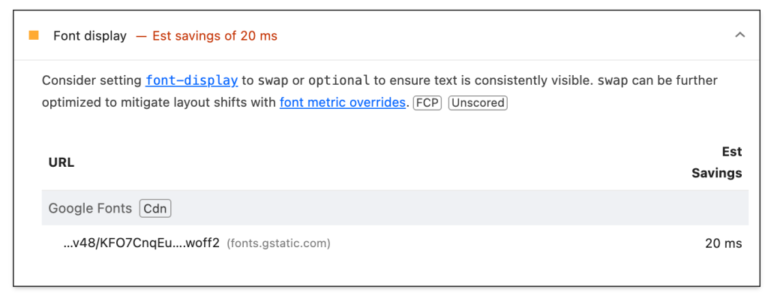
Is your WordPress site failing Core Web Vitals checks despite having optimized images and minified code?…