Most users tap Pay on Android and assume it’s simple. Behind that one tap, your app is juggling PCI rules, device security, fraud checks, and 3DS — usually inside a tight latency budget measured in hundreds of milliseconds.
If all of that logic lives in scattered checks, random API calls, and duplicated business rules, it will eventually break in subtle (and expensive) ways.
You need an architecture that treats risk signals and AI decisions as first-class parts of your Android payment flow, not as an afterthought. This article outlines a secure AI architecture for Android payments that turns device, behavior, and transaction data into real-time decisions — without leaking secrets or slowing checkout.

From Signals to Decisions
Modern risk systems combine four main signal groups:
- Identity – account age, KYC status, previous fraud events, chargeback history
- Device – OS version, integrity checks, rooted / jailbroken hints, emulator flags
- Behavior – login velocity, device switching, unusual time-of-day or location patterns
- Transaction – amount, currency, merchant, country, payment method, MCC
For every payment, the system must quickly answer:
Approve, step up (challenge), or block?
A good architecture makes that decision:
- Explainable – you can say why it happened.
- Auditable – you can prove it later to partners or regulators.
- Resilient – partial failure doesn’t silently approve high-risk traffic.
High-level Architecture
Think in four logical layers, with Android as a trusted but constrained edge:
- Android client – signal collection and hardening
- API and risk gateway
- Real-time risk engine (rules + models)
- Decision, logging, and learning loop
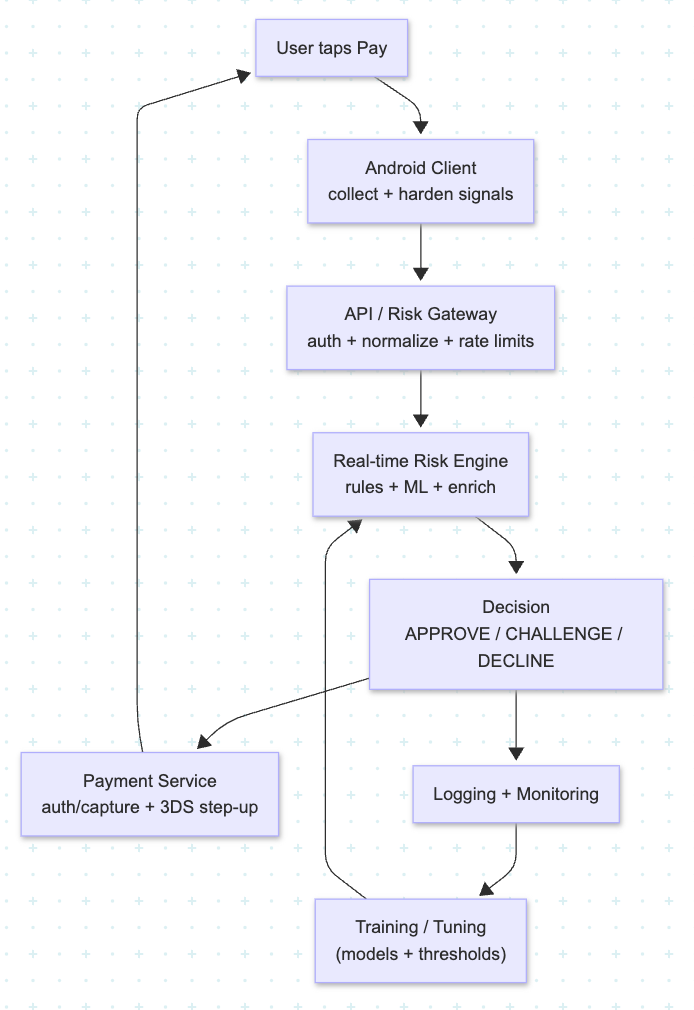
This separation keeps your app lean while still giving risk teams room to move fast.
1. Android Client: Signal Collection and Hardening
On-device, your goals are simple:
- Collect rich but minimal risk signals.
- Protect secrets and prevent tampering.
- Fail safe when checks can’t run.
Common building blocks:
- Secure storage for tokens and device IDs (hardware-backed keystore, encrypted preferences).
- Device integrity checks (Play Integrity / SafetyNet or OEM equivalent).
- Behavior signals: last login time, device change, app version, coarse network and location.
- Payment context: amount, currency, merchant, payment method, “first payment on this device,” and basic cart metadata.
Bundle these into a single RiskContext object and send it to your backend over hardened HTTPS with certificate pinning and strict TLS settings. Don’t leak raw card data here; that belongs in PCI-scoped code paths only.
On errors (can’t read sensors, integrity API fails), the client should:
- Mark the signal as unknown rather than faking a “good” value.
- Let the backend decide how to treat missing data, instead of guessing locally.
2. API and Risk Gateway
The gateway or BFF terminates TLS and normalizes risk traffic:
- Authenticates the app, version, and user.
- Validates payloads and enforces simple anti-abuse protections (rate limits, IP / device throttling).
- Converts different flows (cards, wallets, bank, BNPL) into a standard risk request schema.
Routing risk calls through one gateway gives you:
- A single choke point for emergency controls.
- Cleaner observability (every risky payment crosses this line).
- A place to attach new capabilities (e.g., bot detection) without touching the client.
This is also where you can attach region-specific logic, like extra checks for certain countries or regulatory regimes.
3. Real-Time Risk Engine
This is where streaming data and AI live together. A practical design combines:
- Rules engine– obvious and regulatory controls:
- Block if card is on a deny list.
- Force challenge if amount > threshold and country is new.
- Instantly decline for clearly impossible device fingerprints.
- ML models – transaction-, user-, and device-level risk scores based on historical patterns.
- Aggregations / graphs – velocity checks, device clustering, account linkage, shared IP / device trees.
A request from Android is enriched with:
- Recent transactions and disputes for this account or device.
- Device history (new vs known, past chargebacks).
- External signals (BIN risk, merchant risk, IP reputation).
The engine returns a structured response such as:
{
"decision": "APPROVE | CHALLENGE | DECLINE",
"reason_codes": ["VELOCITY_HIGH", "NEW_DEVICE"],
"risk_score": 0.87,
"step_up": "3DS"
}
Two important points:
- Reason codes feed dashboards, analytics, and customer support tooling.
- Model version + config version should be attached for audit and rollback.
4. Decision, Logging, and Learning
The payment service consumes the risk response:
APPROVE→ continue authorization / capture and show success.CHALLENGE→ trigger 3DS or in-app step-up (OTP, biometric, extra PIN).DECLINE→ fail fast with a clear but non-revealing message (e.g., “We couldn’t complete this payment. Please try another method.”).
Every decision, plus eventual ground truth (chargebacks, disputes, confirmed good users), is logged into:
- A real-time store for monitoring and alerts (spikes in declines, challenge rates, timeouts).
- A data lake / warehouse for model training, rule tuning, and offline analysis.
Over time, those logs feed:
- New and better fraud models.
- Adjusted thresholds per region, segment, or payment type.
- Safer defaults when unknown conditions appear (e.g., new device types or payment methods).
That’s how you close the loop: Android sends signals, the backend decides, and history continuously informs smarter, better-calibrated models.
Wrapping Up
Secure AI for Android payments isn’t “add a model to checkout.” It’s an end-to-end architecture that turns noisy risk signals into fast, explainable, real-time decisions.
If you treat the Android app as a hardened signal collector, centralize risk logic in a dedicated engine, and invest in logging and feedback loops, you get three big wins: less fraud, less friction for good customers, and better evidence for partners, auditors, and regulators when it really matters.