TLDR: Certificate Authorities (CAs) are the ultimate trust brokers online, issuing the digital certificates that make secure web browsing, e-commerce, and confidential communications possible. This article breaks down what CAs do, the nuances of public and private trust, role of browsers and global forums and how they enforce compliance, and why recent security incidents underline the critical responsibility of every CA.
We’ll explore Certificate Transparency (CT), leading CAs and CT log providers, review high-profile failures, and explain where CA technology is headed next.
Introduction
Every time you see a padlock in your browser’s address bar (left to where url is shown) , a sophisticated interplay of trust and technology makes your session secure. Behind the scenes are entities called Certificate Authorities (CAs), entrusted with validating identities and underpinning the encryption that keeps the modern web safe from attackers. But what does it truly mean to be a CA? Why are missteps by CAs headline news? And how do browsers, public log providers, and new standards work together to preserve digital trust (or break them)?
The Digital Certificate Journey: Issuance to Trust
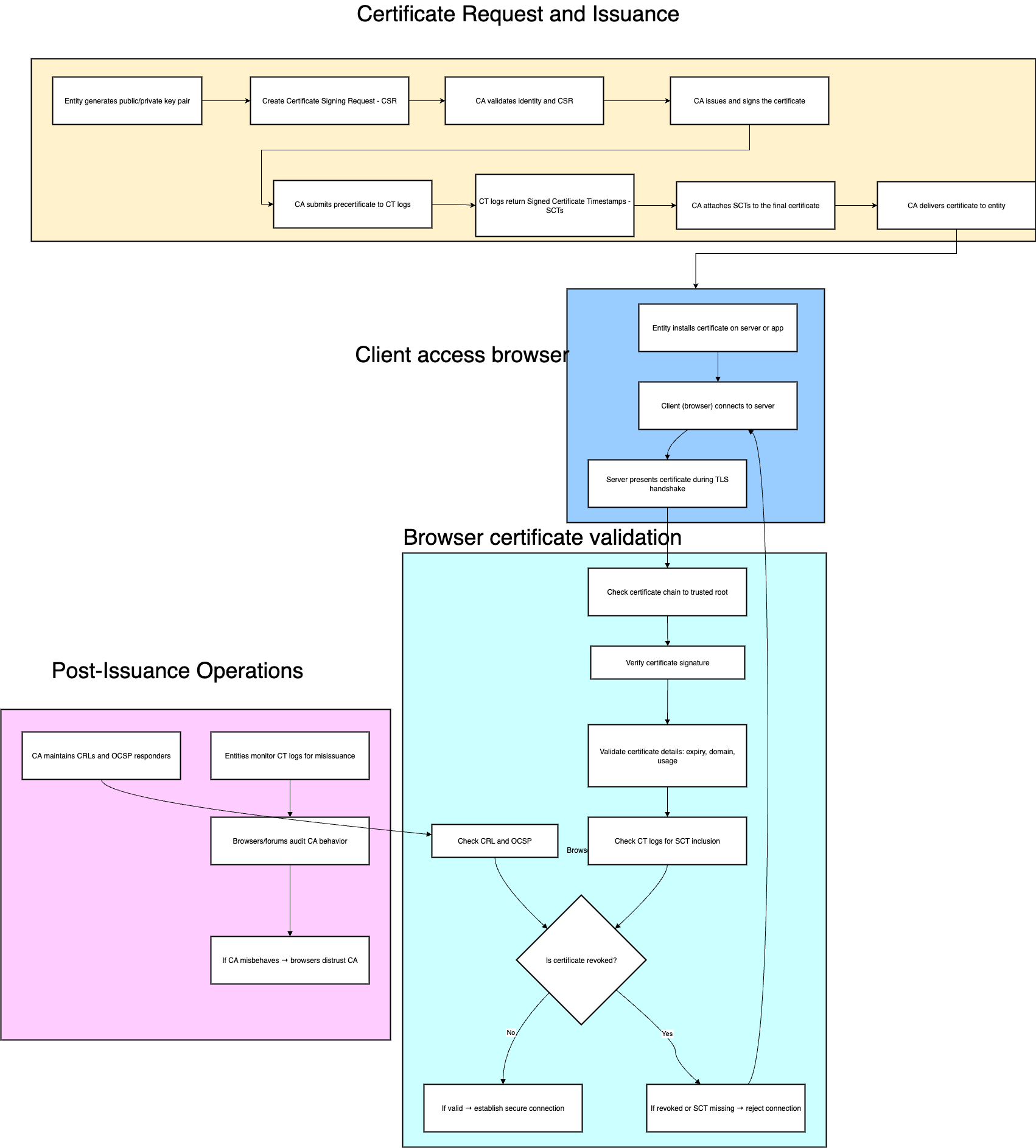
A digital certificate acts like a digital passport: it securely binds a verified entity (such as a website or organization) to a cryptographic key. Here’s how the process works:
- Key Generation: The entity creates a public/private key pair.
- Certificate Signing Request: A Certificate Signing Request (CSR) with the public key and ID details is sent to a CA.
- Rigorous Validation: The CA validates the requester’s legitimacy using accepted industry standards.
- Issuance and Signing: The CA digitally signs the certificate, which browsers and clients can verify.
- Distribution & Revocation: CAs also publish revocation information so expired or compromised certificates don’t undermine trust.
This system is known as the Public Key Infrastructure (PKI)—it is what allows your browser to independently verify a website’s identity.
Who Can a CA Be?—Public vs. Private Trust
Not all CAs are created for the same audience:
Public Trusted CAs:
These are recognized globally, their roots (of the trust chain) hard-coded into browsers and operating systems. Examples include DigiCert, Let’s Encrypt, GlobalSign. They serve anyone needing a certificate trusted on the open internet.
Private Trusted CAs:
These are operated internally by organizations for employee devices, internal services, or IoT deployments. Their certificates are only trusted within their managed environments, not by browsers by default.
Table: Leading Certificate Authorities (2025)
| Certificate Authority | Specialization/Notes |
|---|---|
| DigiCert | Global leader, premium focus, owns Symantec & Thawte |
| GlobalSign | Enterprise and international customers |
| Sectigo (ex-Comodo) | Diverse product range |
| GoDaddy | Major registrar also offering CA services |
| Entrust | Institutional, high-assurance credentials |
| Let’s Encrypt | Free, automated, TLS at scale |
| GeoTrust, Thawte | Both part of DigiCert Group |
| Network Solutions | Established US-based CA |
| RapidSSL | Cost-effective choice for small business |
The Role of Browsers: Gatekeepers of Trust
Browsers don’t blindly trust every CA—they each maintain a root store: a list of CAs whose certificates they accept by default. When a website presents a certificate, browsers verify that its signing CA traces up to one of these trusted roots.
Popular Browser root store and policies :
| Browser | Root Store Used | Notable Policies |
|---|---|---|
| Chrome | Chrome (Google) Root Store | Strict CT enforcement, rapid distrust after incidents |
| Firefox | Mozilla Root Store | Responsive incident handling, CT mandatory |
| Safari | Apple Trust Store | CT enforcement, Apple policies for iOS and macOS |
| Edge | Microsoft Windows Root Store | Follows Windows OS updates |
Browsers also enforce Certificate Transparency (CT) by requiring new certificates to appear in public, append-only logs—a mechanism to detect fraud or CA mistakes.
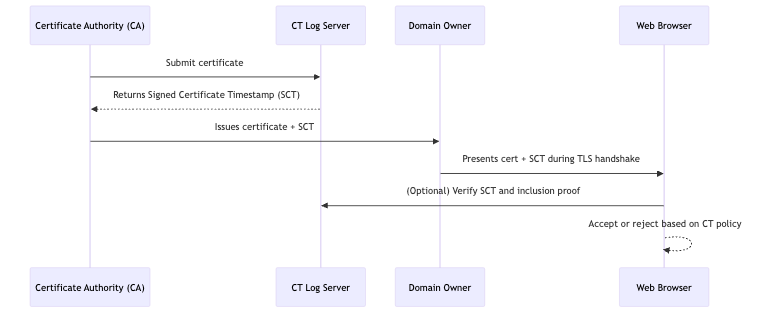
What Is Certificate Transparency?
Certificate Transparency (CT) is a security standard developed by Google to make SSL/TLS certificates more trustworthy and detect fraudulent/misissued certificates. It introduces public, append-only logs that record all certificates issued by Certificate Authorities (CAs).
Before CT:
- Browsers trusted any valid certificate issued by a trusted CA.
- CAs could accidentally (or maliciously) issue certificates for domains they don’t control.
- Domain owners had no way to know if someone else got a cert for their domain.
With CT:
- All new SSL/TLS certificates must be publicly logged.
- Anyone can monitor these logs to detect unauthorized certificates.
- Browsers (like Chrome) can reject certs not logged in CT.
We need Certificate Transparency and all major browsers enforce it due to:
- Detect MisIssuance: CT allows domain owners to catch if a CA issues a cert for their domain without authorization
- Enforce CA Accountability: All certs are publicly auditable.
- Prevent MITM Attacks: CT helps browsers detect shady certs early and block them.
- Improve Web Trust: Promotes a healthier PKI ecosystem by reducing blind trust in CAs.
Best place to know more about CTLogging are: https://certificate.transparency.dev/ and forums like https://groups.google.com/g/certificate-transparency.
Key Forums and the Policy Landscape
Certificate Authorities (CAs) operate under rules set by international standards bodies and consortiums. The CA/Browser Forum, for example, establishes the Baseline Requirements that govern certificate issuance, validation processes, and operational practices for all publicly trusted CAs. The Internet Engineering Task Force (IETF) is responsible for defining technical standards, such as RFCs that underpin protocols like Certificate Transparency. Additionally, regional or national entities such as eIDAS in the EU or the US Federal PKI oversee policy and compliance for public sector and government roots.
These organizations and forums are crucial because they continually refine requirements for identity validation, certificate lifetimes, and transparency measures. Their collective efforts drive both compliance and ongoing innovation within the web’s trust infrastructure.
CA Failures: Public Incidents and Industry Lessons
The integrity of digital trust is fragile—when a CA fails, the consequences reverberate throughout the entire internet. There have been several major incidents where CAs have been compromised or breached industry rules:
- In 2011, DigiNotar was hacked, leading to the issuance of hundreds of fraudulent certificates, many of which were used for man-in-the-middle attacks against users in Iran. The fallout was so severe that DigiNotar lost all browser trust and ultimately went bankrupt.
- Symantec, over the period from 2015 to 2018, repeatedly violated industry requirements, issuing unauthorized or improperly validated certificates. As a result, all major browsers removed Symantec’s root certificates, forcing millions of businesses to replace their digital certificates.
- WoSign and StartCom were distrusted in 2016 after policy violations, including certificate backdating and improper controls, came to light.
- In 2015, CNNIC, the China Internet Network Information Center, delegated excessive authority to a third party, resulting in unauthorized certificates for high-profile domains. This caused browsers to blacklist CNNIC’s roots.
- Recent years have also seen compliance failures threaten the status of other major CAs, such as “Entrust”, leading to announcements of root certificate removal from trusted stores.
When trust in a CA is lost, all certificates it has issued must be replaced (after revoking older ones), disrupting service for countless organizations and underscoring the critical nature of CA operations.
Why Not Everyone Can Be a CA
Operating a publicly trusted CA is about far more than deploying technical systems. Aspiring CAs must pass strict legal, technical, and policy reviews, undergo regular independent audits, and maintain robust monitoring to detect irregularities in real time. The operational burden includes constant incident response readiness and the need for complete transparency around mistakes or misissuances.
Failure to meet the high bar set by the CA/Browser Forum or to maintain compliance with Certificate Transparency requirements can result in complete disqualification from all browser root programs—a commercial death sentence for any CA.
For those interested in the field, it’s wise to experiment with private CA set-ups, participate in open-source PKI projects, and deepen their understanding of this complex regulatory and technical landscape.
The Future of the CA Ecosystem
The Certificate Authority (CA) ecosystem is evolving rapidly to meet emerging security challenges and scalability demands. Key trends shaping the future include:
- Quantum-Resistant Cryptography:
As quantum computing advances, traditional cryptographic algorithms risk becoming vulnerable. The CA industry is actively exploring and preparing to deploy quantum-resistant algorithms to safeguard digital trust against these future threats. - Shorter Certificate Lifetimes and Automation:
To reduce the attack window from compromised certificates, industry standards are driving a phased reduction in TLS certificate lifetimes—from 398 days today, down to 200 days in 2026, 100 days in 2027, and ultimately 47 days by 2029. In parallel, automation tools are enabling rapid certificate issuance and renewal. Let’s Encrypt, for example, now offers optional six-day certificates alongside their traditional 90-day certificates, pushing the envelope on minimizing risk. - Next-Generation Certificate Transparency (CT) Logging:
Traditional CT logs face scalability and cost challenges due to their dynamic, append-only design. The emergence of static CT logs, such as the Sunlight project by Let’s Encrypt and partners, uses cacheable data tiles served via object storage and CDNs. This innovation enhances performance, reliability, and accessibility—making public monitoring of certificates more efficient while maintaining strong transparency and trust.
(References: https://sunlight.dev, Let’s Encrypt Sunlight reflections) - Scaling Machine and IoT Identity Management:
As connected devices, APIs, and automated services proliferate, managing their identities securely at scale is critical. CAs are evolving to support this growing ecosystem, offering streamlined, automated certificate issuance and lifecycle management tailored to machine identities. - Instant Revocation and Real-time Security Controls:
To quickly mitigate compromise risks, the deployment of automated, instantaneous certificate revocation mechanisms—leveraging Online Certificate Status Protocol (OCSP) and emerging standards—is gaining momentum. Faster revocation improves overall ecosystem resilience. - Decentralized Trust Models and AI-Driven Monitoring:
Research into alternative trust models strives to address the inherent centralization risks of current PKI systems. Decentralized ledgers, blockchain-inspired roots, and AI-powered anomaly detection tools are in active exploration, aiming to enhance transparency, trustworthiness, and early detection of mis-issuance or fraud.
Collaborative Ways to Advance Trust
Individuals and organizations can all contribute to a safer internet:
- Monitor Certificate Transparency logs for their domains to spot unauthorized certificates.
- Audit their trust stores regularly and remove root CAs that are obsolete or unnecessary.
- Stay engaged with community standards—vote in CA/Browser Forum ballots, review IETF drafts, and pay attention to security bulletins from browser vendors.
- Educate teams and colleagues about the meaning and validation of digital certificates and browser trust indicators.
References and Further Reading
To stay informed, some of the useful resources:
- Review Baseline Requirements and incident reports at the CA/Browser Forum
https://cabforum.org/working-groups/server/baseline-requirements/
https://cabforum.org/proceedings/documents/ - Read relevant IETF RFCs
CT 2.0: https://datatracker.ietf.org/doc/html/rfc9162
CT 1.0 : https://www.rfc-editor.org/rfc/rfc6962 (Note that browsers like chrome still only supports rfc 6962) - Browser Root Programs:
Google Chrome Root Program and CT Enforcement:
https://chromium.googlesource.com/chromium/src/+/refs/heads/main/docs/root_store/root_store_policy.md
Mozilla Root Program:
https://wiki.mozilla.org/CA/Root_Store_Policy
Apple Root Certificate Program:
https://support.apple.com/en-us/HT209143
Microsoft Trusted Root Program:
https://aka.ms/rootcertprogram - Certificate Transparency Log Providers and Monitoring Dashboards:
Google Certificate Transparency:
https://transparencyreport.google.com/https/certificates
Cloudflare CT Logs:
https://www.cloudflare.com/certificate-transparency/ - Industry News and Incident Analysis:
The Register – Security Section:
https://www.theregister.com/security/
Krebs on Security (Brian Krebs) – Investigative reports on CA incidents:
https://krebsonsecurity.com/